Neste artigo iremos ensinar os usuários e administradores de rede, como verificar se sua placa de rede contem pacotes perdidos através do alguns comando no Linux.
Podemos usar o comando ip ou o comando netstat ou o comando ethtool para mostrar estatísticas de pacotes perdidos ou descartados por interface de rede no Linux. Vamos ver como usar os pacotes descartados da lista de comandos por interface.
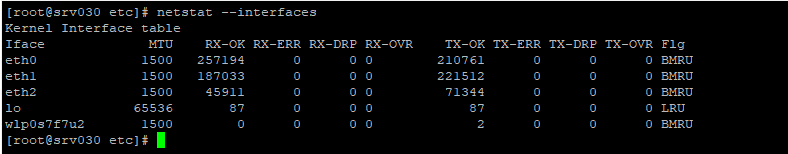
Exibindo pacotes perdidos por interface no Linux usando o netstat
O comando netstat é quase sempre obsoleto. A substituição do netstat é o comando ss e ip. No entanto, o netstat ainda está disponível em distros Linux mais antigas, que estão em produção. Portanto, começarei com o netstat, mas se possível, use as ferramentas ip / ss. A sintaxe é:
OU
Netstat mostra pacotes descartados por interface no Linux
Exibindo estatísticas de rede por interface de rede no Linux
OU
Ip:
469791 total packets received
254393 forwarded
0 incoming packets discarded
213598 incoming packets delivered
495020 requests sent out
16109 outgoing packets dropped
21 dropped because of missing route
8 reassemblies required
4 packets reassembled ok
4 fragments received ok
8 fragments created
Icmp:
3858 ICMP messages received
33 input ICMP message failed.
ICMP input histogram:
destination unreachable: 1372
redirects: 29
echo requests: 9
echo replies: 2448
7642 ICMP messages sent
0 ICMP messages failed
ICMP output histogram:
destination unreachable: 4232
echo request: 3401
echo replies: 9
IcmpMsg:
InType0: 2448
InType3: 1372
InType5: 29
InType8: 9
OutType0: 9
OutType3: 4232
OutType8: 3401
Tcp:
30674 active connections openings
1204 passive connection openings
167 failed connection attempts
17119 connection resets received
12 connections established
187415 segments received
235175 segments send out
3079 segments retransmited
0 bad segments received.
17498 resets sent
Udp:
22093 packets received
59 packets to unknown port received.
0 packet receive errors
22824 packets sent
0 receive buffer errors
0 send buffer errors
UdpLite:
TcpExt:
204 invalid SYN cookies received
17 resets received for embryonic SYN_RECV sockets
598 TCP sockets finished time wait in fast timer
2996 delayed acks sent
3 delayed acks further delayed because of locked socket
Quick ack mode was activated 1672 times
30 SYNs to LISTEN sockets dropped
20 packets directly queued to recvmsg prequeue.
4 bytes directly received in process context from prequeue
27509 packet headers predicted
34928 acknowledgments not containing data payload received
35372 predicted acknowledgments
74 times recovered from packet loss by selective acknowledgements
110 congestion windows recovered without slow start by DSACK
79 congestion windows recovered without slow start after partial ack
TCPLostRetransmit: 8
20 timeouts after SACK recovery
1 timeouts in loss state
157 fast retransmits
16 forward retransmits
35 retransmits in slow start
13423 other TCP timeouts
TCPLossProbes: 1068
TCPLossProbeRecovery: 287
6 SACK retransmits failed
1760 DSACKs sent for old packets
11 DSACKs sent for out of order packets
753 DSACKs received
6 DSACKs for out of order packets received
29938 connections reset due to unexpected data
8 connections reset due to early user close
118 connections aborted due to timeout
TCPDSACKIgnoredOld: 8
TCPDSACKIgnoredNoUndo: 184
TCPSpuriousRTOs: 22
TCPSackShifted: 324
TCPSackMerged: 539
TCPSackShiftFallback: 361
IPReversePathFilter: 8
TCPRetransFail: 9967
TCPRcvCoalesce: 7269
TCPOFOQueue: 610
TCPOFOMerge: 11
TCPChallengeACK: 5
TCPSpuriousRtxHostQueues: 4083
TCPFromZeroWindowAdv: 3
TCPToZeroWindowAdv: 3
TCPWantZeroWindowAdv: 39
TCPSynRetrans: 223
TCPOrigDataSent: 130452
TCPHystartDelayDetect: 8
TCPHystartDelayCwnd: 547
TCPACKSkippedSeq: 1
IpExt:
InNoRoutes: 1
InBcastPkts: 714
InOctets: 391519325
OutOctets: 667667104
InBcastOctets: 113497
InNoECTPkts: 470034
InECT0Pkts: 666
Para exibir estatísticas resumidas para cada protocolo, execute:
Mostra estatísticas TCP
netstat -s -t
Mostra estatísticas UDP
netstat -s -u
Mostra estatísticas através do comando ethtool
Sintaxe:
Exemplo:
NIC statistics:
tx_bytes: 0
rx_bytes: 0
tx_broadcast: 0
rx_broadcast: 0
tx_multicast: 0
rx_multicast: 0
tx_unicast: 0
rx_unicast: 0
tx_mac_pause: 0
rx_mac_pause: 0
collisions: 0
late_collision: 0
aborted: 0
single_collisions: 0
multi_collisions: 0
rx_short: 0
rx_runt: 0
rx_64_byte_packets: 0
rx_65_to_127_byte_packets: 0
rx_128_to_255_byte_packets: 0
rx_256_to_511_byte_packets: 0
rx_512_to_1023_byte_packets: 0
rx_1024_to_1518_byte_packets: 0
rx_1518_to_max_byte_packets: 0
rx_too_long: 0
rx_fifo_overflow: 0
rx_jabber: 0
rx_fcs_error: 0
tx_64_byte_packets: 0
tx_65_to_127_byte_packets: 0
tx_128_to_255_byte_packets: 0
tx_256_to_511_byte_packets: 0
tx_512_to_1023_byte_packets: 0
tx_1024_to_1518_byte_packets: 0
tx_1519_to_max_byte_packets: 0
tx_fifo_underrun: 0
Conclusão
Agora você poderá verificar de maneira simples o problema de pacotes perdidos no Linux, como também avaliar como está a saúde de suas interfaces de rede. Segue mais alguns artigos relacionados.
Dica de como configurar login SSH sem senha
7 aplicativos para monitorar o Linux em 2020